The wireless home network technology is dominated by the WiFi brand (WiFi=Wireless Fidelity) which is based on the IEEE 802.11 standard. There exist different versions of the 802.11 standard (a,b,g,n) with different characteristics, as shown on this Post.
A typical WiFi wireless home network is shown below:
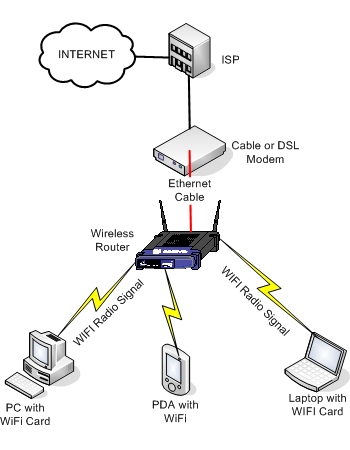
The heart of the wireless network is the WiFi wireless router, which controls all wireless devices (Laptops, PCs, PDAs etc) and routes the traffic to the wired (Ethernet) connection. All wireless devices have to be equipped with a compliant 802.11 WiFi wireless adapter card. These adapters can be embedded in the device, or can be externally attached (USB, PCMCIA).
Equipment Checklist
Wireless Router:
This is the gateway between the wired and wireless world. It takes the wired ethernet data coming on its ethernet port and translates that data to radio signals for transmitting to the attached wifi devices, and vica-versa. It also assigns IP addresses to the attached wireless devices and routes traffic between them, and between the wireless and wired interfaces. This router also facilitates Internet Connection Sharing by connecting its wired Ethernet port to the ADSL/Cable modem of the Internet Service Provider (ISP). The wireless router controls also the security of the wireless home network. You can configure SSID, WEP, WAP, MAC Filtering etc to secure and control which devices can be attached on the wireless network (more info below).

Wireless Adapter:
Each wifi device must be equipped with a wireless network adapter. Almost all modern laptop computers come with an embedded wireless adapter, but you can also connect external devices (USB, PCMCIA) as shown below. Once you install the drivers of the wireless adapter and configure it properly, it should start searching for available wifi routers in the area in order to attach on the network. By default, if you didn’t do any configuration on the wifi router (i.e you left it with its default configuration and turned it on), the wireless adapter should automatically attach to the wireless router, get an IP address, and should be fully connected to the wireless network. However, leaving your wifi network configured with its default (out of the box) settings is not secure at all. Some basic security must be applied, as we will see below.
 |
 |
Typical Configuration
SSID:
The Service Set Identifier (SSID) is the name of each particular wireless network. All wireless devices of the same network must have the same SSID in order to communicate with each other. The SSID is configured first on the wireless router, and then on each client device. If the SSID is left unspecified, then any wireless device can connect on the wireless network, which is not a good security practice. The image below shows a typical SSID configuration on a wireless router.
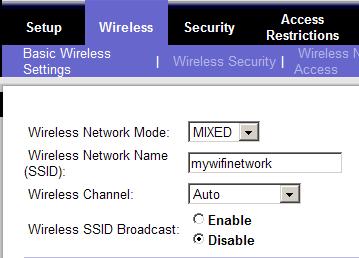
The SSID name “mywifinetwork” must be configured on all wireless devices of this particular wifi home network in order to communicate with each other. Another important security enhancement is to Disable the Wireless SSID Broadcast, so that the router does not transmit out on free air the SSID name.
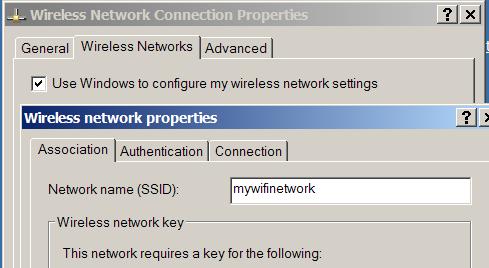
The image below shows the SSID configuration settings on a WinXP laptop computer with wireless network adapter. You configure the SSID under
“Network Connections> right click on Wireless Network Connection> Properties> Wireless Networks> Add “. As you can see, the SSID name configured on the laptop is the same as the SSID on the wireless router.
Security:
One of the disadvantages of wireless networks is weak security. If you connect your wireless equipment with default settings, then you will manage to provide your neighbor with free internet access as well!!
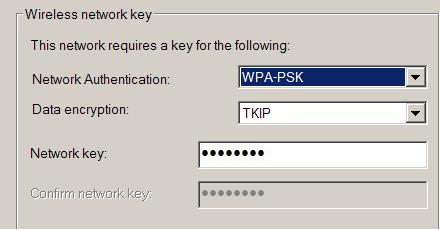
Fortunately, the WiFi alliance has developed several security techniques to provide encryption and access control to the wireless network. One of these security techniques is WiFi Protected Access (WPA) with Preshared Key (PSK). To configure WPA with PSK, you need to enable it on both the router and the client, and also configure a common pre-shared key between them. The settings on the router are shown below:
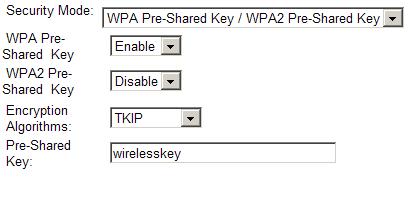
The Pre-shared key “wirelesskey” (together with enabling WPA-PSK) must be configured also on the laptop wireless adapter, as shown below:
TCP/IP Network Settings:
As far as tcp/ip network settings are concerned, by default the wireless router works also as a DHCP server, which means that it assigns IP addresses dynamically to the wireless clients. Basically you don’t need to configure anything for the tcp/ip network settings, since each client will automatically receive an IP address from the wireless router.
Use your Wireless Home Network to Monitor your Home
One of the benefits of having a wireless network in your home is that you can install wireless security cameras for monitoring the inside of your home from anywhere in the world. This is discussed in more detail in this post. Linksys has several products for home camera security such as the one shown below:

The Linksys Wireless-G Pan/Tilt/Zoom Video Camera sends live video through the Internet to a web browser anywhere in the world! The Pan/Tilt/Zoom feature gives also flexible control remotely from a Web Browser. If you enable the security mode of the camera, you can also use it as a motion detection sensor, which can send you email alerts with video clips upon motion detection.
i have a shop around 2hunder feet away without digging what can i do to get wifi out there